Working with data is the point of a computer system in the first place, and securing that data has never been more important.
Cybersecurity is like the old saying about project status: “Steady progress, never closer.” It’s hard to escape the message that cybersecurity has never been as important as it is today, even if we’re not paying attention to the daily headlines about ransomware, data theft, security breaches, and so on. And cybersecurity will be even more critical tomorrow and in the days to come. The escalation of threat vs. defense will continue, hence the view that while we’re making progress, and while we’ve never been closer to a solution, we’ll never quite reach that final destination.
Cybersecurity may not be the first thing you think about when designing a computer system but—in the long run—it is likely more important than choosing the CPU, motherboard design, graphics processor, I/O ports, etc. After all, working with data is the point of a computer system in the first place, and securing that data has never been more important.
But first, what is DAR?
Like any other specialty, the world of cybersecurity and data protection includes a lot of jargon. For example, the term “data at rest” or “DAR” refers to what most of us just think of as “data”; that is, data stored on our computer’s SSD, external hard drive, on our phones, or in the cloud. DAR is one of three data states, another of which is data in flight, that is, data being transmitted within a computer or between systems. The third state is data in use, or data that is actively being updated, processed, accessed, erased, or read by a system.
When many of us think about cybersecurity and protecting ourselves from ransomware, we think about anti-virus software, spam filters, and passwords more complex than “password123.” Many organizations with sensitive data, especially those that have regulatory requirements or security protocols, have expanded their cyber focus to include protecting data at rest. This includes the US Government. In the spring of 2021, President Biden issued an Executive Order that, among other mandates, called for encrypting and securing data at rest.
Use SEDs!
While the selection of many, if not most, computer components is neutral to addressing cyberthreats, there are a few elements that greatly enhance data security, starting with the choice of internal SSD or hard drive.
New computer system designs likely take advantage of speedy NVMe SSDs using PCIe Gen 3 or Gen 4 protocol in the M.2 form factor; others may use 2.5-inch SSDs or even traditional rotating media hard drives. While speed and capacity matter, system designers should consider whether to use a self-encrypting drive (SED). An SED incorporates hardware technology to encrypt data as it is being stored and decrypt it as the data is read. If an encrypted drive is separated from its host computer, its 256-bit AES encryption will ensure it would take millions of years for the most powerful quantum computer to decipher the data.
When choosing a SED, select a FIPS-certified device, perhaps even a Common Criteria (CC) and NIAP-listed unit. FIPS stands for Federal Information Processing Standards, which are maintained by the National Institute of Standards and Technology (NIST). NIST developed FIPS for use in computer systems by non-military American government agencies and government contractors. NIAP is the National Information Assurance Partnership, the organization responsible for the US implementation of the Common Criteria.
Remember removables
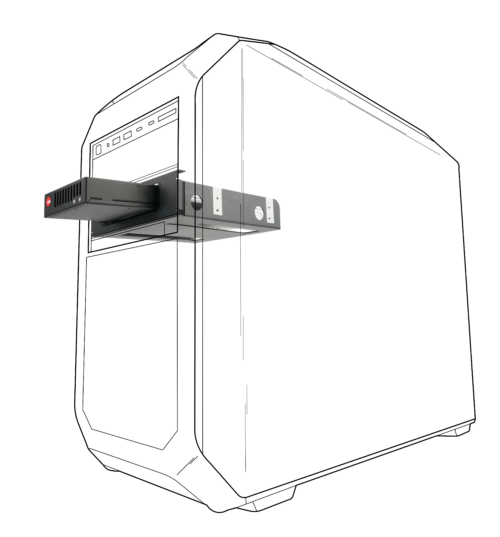
Another security-enhancing choice is to specify a computer chassis that has at least one drive bay that can be dedicated to easily integrated removable drives. Removable drives are useful for separating the hard drive or SSD from the system (one way to air gap your data).
Many organizations have specific policies and procedures that require the use of removable drives for physically securing data by locking them up in safes or for use in secure facilities. In addition, removable drives are often used in creating onsite/offsite backup workflows or in transporting large amounts of data.
Protect your boot drive with PBA
Encrypting data is a good step to keeping it private. Going hand-in-hand with encryption is pre-boot authentication (PBA) technology. PBA requires that a computer user enter authorized login credentials to the SSD itself before the computer will even recognize that the SSD is present. After all, if the computer can’t see that the drive exists, it can’t be read or attacked.
PBA precedes the normal startup procedure such that a user is communicating directly with the SSD for the authentication process. Once proper authorization is obtained, the computer recognizes the presence of the SSD and continues with its boot sequence.
Double things up with MFA
But wait, there’s more. A good PBA will employ multi-factor authentication (MFA) in its startup process. MFA, also known as two-factor authentication or 2FA, augments the username-password combo with another credential. MFA is a combination of the following:
• Something the user has, such as a security token or key.
• Something the user is, such as a fingerprint, voice, or even typing speed.
• Something the user knows, such as a password.
• Somewhere the user is, such as a GPS coordinate.
Hardware security dongles (a YubiKey, for example) contain a license key or some other cryptographic protection mechanism that the user plugs into a USB port. Some organizations do not allow active USB ports in their computer systems. In the case of organizations like federal agencies and the DoD (including civilian employees and contractor personnel), a common option is to employ a smartcard called a Common Access Card (CAC), which will require the system to be equipped with an appropriate card reader.
System design is holistic
Not surprisingly, we get so focused on “the latest and greatest” or on using technology to solve our problems that we often neglect the human part of the equation. We have predictable habits. We choose easily guessed shortcuts.
Technology does its best: Think about some of the ways in which we use security tools today that we didn’t know about just a few short years ago: fingerprint or facial recognition to unlock our smartphones, for example, or receiving a security code via text message or email to make sure that you are you when logging into your credit card website.
These now-commonplace measures can be bolstered with secure data storage in everyday laptop and desktop computer systems. The more system designers use these components while thinking ahead to the cyber challenges that will continue to be with us, the more secure our systems and our data will be.